
File Sharing & Tracking
File Sharing & Tracking
Securely share documents, monitor real-time access, and maintain full control with enterprise-grade tracking and encryption.

End-to-End Encrypted

Trackable Share Links

Digital Fingerprinting

256-bit
AES Encryption

100%
Traceable

2
Share Methods

∞
Unlimited Recipients
Controlled File Sharing
Choose how you distribute documents with full control and tracking capabilities

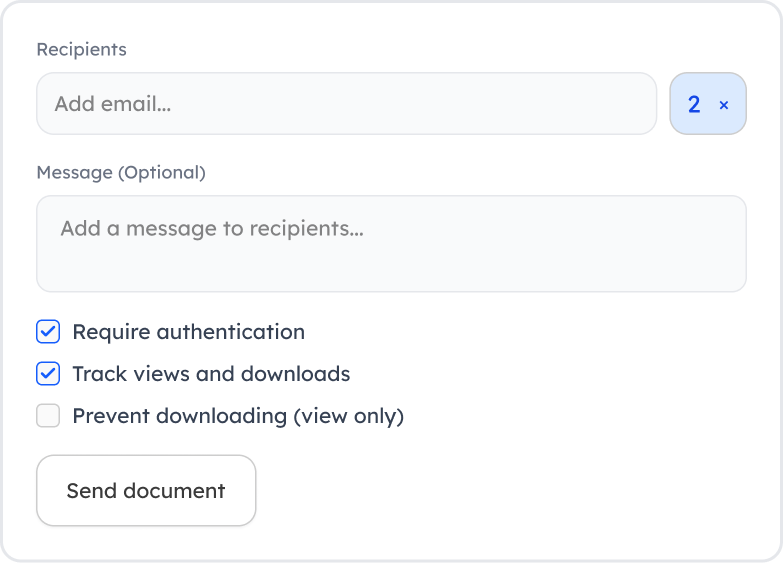
Email Sharing
Distribute documents securely via email with automatic tracking and access controls.
Ideal for internal collaboration and audit-compliant exchanges.

Link Sharing
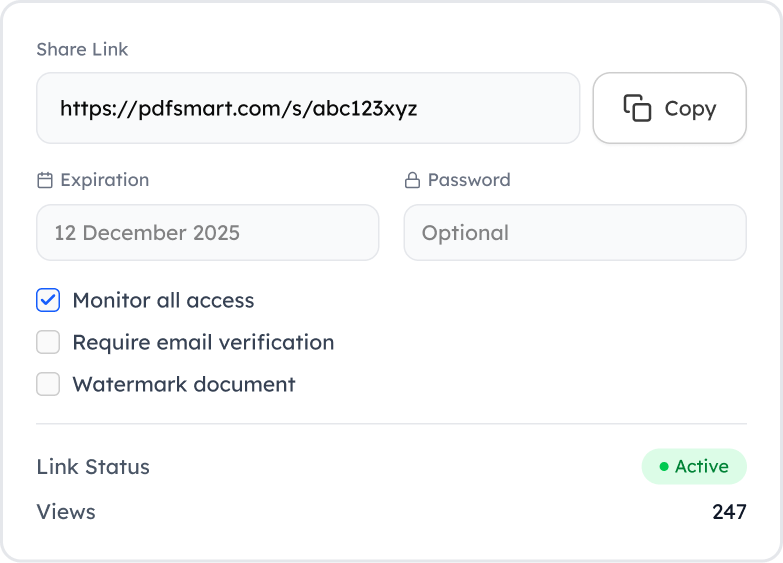
Generate secure, traceable links for documents that can be revoked anytime.
Designed for external distribution and time-limited access.
Common Security Controls

Access Expiration
Set automatic expiration dates

Audit Tracking
Access audit logs and activity

Password Protection
Secure with passwords

Revocable Links
Instant link revocation

Enterprise Exclusive
Enterprise Protection Features
Comprehensive tracking and security for your most sensitive documents

Unique Digital Fingerprints
Assign a traceable fingerprint to every shared file.
Every share creates a unique, forensic-grade digital fingerprint that survives format conversion, printing, and even screenshots.

Automated Leak Detection
Detect and alert unauthorized document sharing.
Continuous monitoring alerts you to potential unauthorized sharing or leaks, enabling rapid response to security incidents.

Forensic Legal Evidence
Provide legally defensible proof in compliance audits.
Forensic-grade tracking provides admissible evidence for legal proceedings and compliance audits with full chain of custody.
Digital Fingerprinting is available exclusively for enterprise accounts under advanced security licensing.

Advanced Security
Digital Fingerprinting with Steganography
Invisible watermarking for traceability and compliance in sensitive document exchanges.
Protect your sensitive documents with invisible digital watermarks. Each shared file contains a unique, hidden fingerprint that allows you to monitor the document's origin if it's leaked or shared without authorisation.

Full Traceability
Trace any leaked document back to the exact share link, recipient, and timestamp

Tamper Resistant
Fingerprints survive format conversion, printing, and scanning. Even screenshots retain identifiable markers

Invisible to Users
Steganographic watermarks are completely invisible and don't affect document quality or file size
Designed for GDPR compliant environments.
How It Works
1
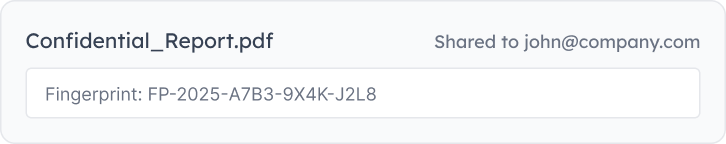
Document Shared
When you share a document, a unique digital fingerprint is embedded
2
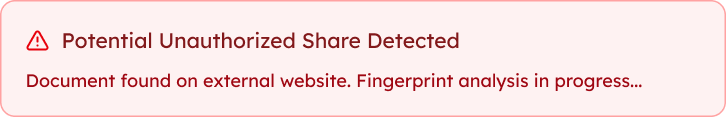
Document Leaked
If the document is leaked or shared without authorization, you're alerted
3
Source Identified
The fingerprint reveals exactly who received the original document

